Quick start
Prerequisites
The prerequisites for connecting an AWS Kinesis sink connector to external systems include:- Create a Kinesis data stream in AWS.
- Create an AWS User and an
AccessKey(Please record the value ofAccessKeyand itsSecretKey). - Assign the following permissions to the AWS User:
- AmazonKinesisFullAccess
- CloudWatch:PutMetricData: it is required because AWS Kinesis producer will periodically send metrics to CloudWatch.
1. Create a connector
The following command shows how to use pulsarctl to create abuiltin connector. If you want to create a non-builtin connector,
you need to replace --sink-type kinesis with --archive /path/to/pulsar-io-kinesis.nar. You can find the button to download the nar package at the beginning of the document.
If you are a StreamNative Cloud user, you need set up your environment first.
--sink-config is the minimum necessary configuration for starting this connector, and it is a JSON string. You need to substitute the relevant parameters with your own.
If you want to configure more parameters, see Configuration Properties for reference.
You can also choose to use a variety of other tools to create a connector:
- pulsar-admin: The command arguments for
pulsar-adminare similar to those ofpulsarctl. You can find an example for StreamNative Cloud Doc. - RestAPI: You can find an example for StreamNative Cloud Doc.
- Terraform: You can find an example for StreamNative Cloud Doc.
- Function Mesh: The docker image can be found at the beginning of the document.
2. Send messages to the topic
If your connector is created on StreamNative Cloud, you need to authenticate your clients. See Build applications using Pulsar clients for more information.
3. Show data on AWS Kinesis console
You can use the AWS KinesisData Viewer to view the data. 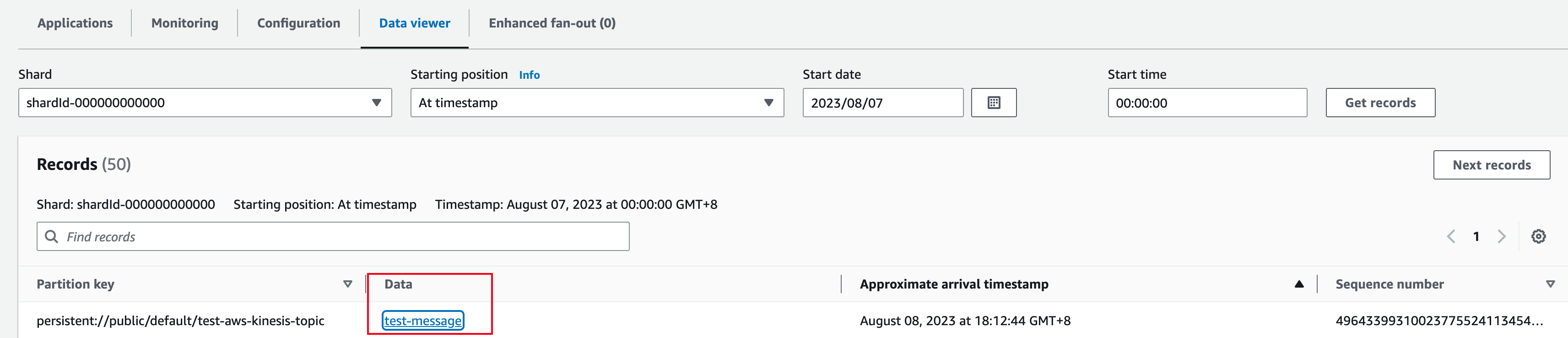
Configuration Properties
This table outlines the properties of an AWS Kinesis sink connector.| Name | Type | Required | Sensitive | Default | Description |
|---|---|---|---|---|---|
awsKinesisStreamName | String | true | false | ” ” (empty string) | The Kinesis stream name. |
awsRegion | String | true | false | ” ” (empty string) | The AWS Kinesis region. Example: us-west-1, us-west-2. |
awsCredentialPluginName | String | false | false | ” ” (empty string) | The fully-qualified class name of implementation of AwsCredentialProviderPlugin. Please refer to [Configure AwsCredentialProviderPlugin](###Configure AwsCredentialProviderPlugin) |
awsCredentialPluginParam | String | false | true | ” ” (empty string) | The JSON parameter to initialize awsCredentialsProviderPlugin. Please refer to [Configure AwsCredentialProviderPlugin](###Configure AwsCredentialProviderPlugin) |
awsEndpoint | String | false | false | ” ” (empty string) | A custom Kinesis endpoint. For more information, see AWS documentation. |
retainOrdering | Boolean | false | false | false | Whether Pulsar connectors retain the ordering when moving messages from Pulsar to Kinesis. |
messageFormat | MessageFormat | false | false | ONLY_RAW_PAYLOAD | Message format in which Kinesis sink converts Pulsar messages and publishes them to Kinesis streams. Available options include: ONLY_RAW_PAYLOAD: Kinesis sink directly publishes Pulsar message payload as a message into the configured Kinesis stream. FULL_MESSAGE_IN_JSON: Kinesis sink creates a JSON payload with Pulsar message payload, properties, and encryptionCtx, and publishes JSON payload into the configured Kinesis stream.FULL_MESSAGE_IN_FB: Kinesis sink creates a flatbuffers serialized payload with Pulsar message payload, properties, and encryptionCtx, and publishes flatbuffers payload into the configured Kinesis stream. FULL_MESSAGE_IN_JSON_EXPAND_VALUE: Kinesis sink sends a JSON structure containing the record topic name, key, payload, properties, and event time. The record schema is used to convert the value to JSON. |
jsonIncludeNonNulls | Boolean | false | false | true | Only the properties with non-null values are included when the message format is FULL_MESSAGE_IN_JSON_EXPAND_VALUE. |
jsonFlatten | Boolean | false | false | false | When it is set to true and the message format is FULL_MESSAGE_IN_JSON_EXPAND_VALUE, the output JSON is flattened. |
retryInitialDelayInMillis | Long | false | false | 100 | The initial delay (in milliseconds) between retries. |
retryMaxDelayInMillis | Long | false | false | 60000 | The maximum delay(in milliseconds) between retries. |
Configure AwsCredentialProviderPlugin
AWS Kinesis sink connector allows you to use three ways to connect to AWS Kinesis by configuringawsCredentialPluginName.
- Leave
awsCredentialPluginNameempty to get the connector authenticated by passingaccessKeyandsecretKeyinawsCredentialPluginParam.
-
Set
awsCredentialPluginNametoorg.apache.pulsar.io.aws.AwsDefaultProviderChainPluginto use the default AWS provider chain. With this option, you don’t need to configureawsCredentialPluginParam. For more information, see AWS documentation. -
Set
awsCredentialPluginNametoorg.apache.pulsar.io.aws.STSAssumeRoleProviderPluginto use the default AWS provider chain, and you need to configureroleArnandroleSessionNmaeinawsCredentialPluginParam. For more information, see AWS documentation



































