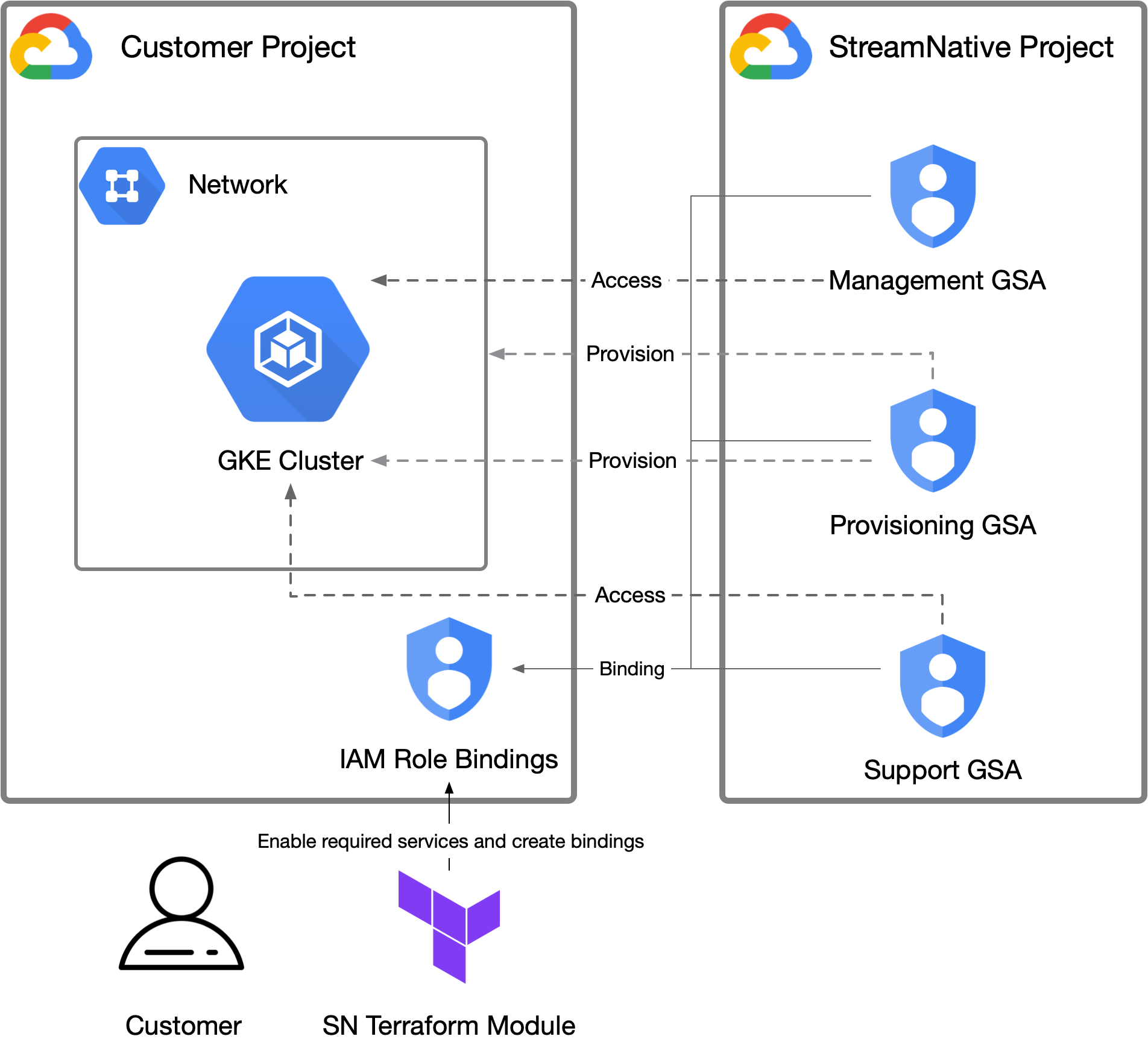
Access model in Google Cloud
StreamNative Cloud leverages GCP’s IAM role bindings to manage access to customer’s projects, allowing for efficient management of only necessary resources. Access to customer projects is segmented into three Google Service Accounts (abbr.GSA):
-
Provisioning GSA: This service account handles the provisioning and maintenance of the underlying infrastructure like DNS Zone, VPCs, GKE clusters (and associated node groups, and so on). Default to
pool-automation@sncloud-production.iam.gserviceaccount.com. -
Management GSA: This service account is primarily for automated management tasks, the core responsibility of this service account is interact with the GKE cluster to deploy and manage Pulsar clusters. Default to
cloud-manager@sncloud-production.iam.gserviceaccount.com. -
Support GSA: This service account is used by the StreamNative SRE and Support team for troubleshooting during incidents. Default to
cloud-support-general@sncloud-production.iam.gserviceaccount.com.
Provision Google Cloud Access
StreamNative facilitates the setup of necessary service accounts and permissions via a module. This module can be provisioned in a standalone Terraform project (as documented here), but can also be integrated into existing Terraform projects. For full documentation of inputs and outputs of the Terraform module, see the module’s README on GitHub.Prerequisites
- New to Terraform? Learn the Terraform Google Cloud Getting Started Tutorial to get a basic introduction.
- Install Terraform, version 1.3.0 or greater.
- Ensure you have created an organization through the StreamNative Cloud Console.
Step 1: Create a new project and instantiate the module
Terraform works by having Terraform codes (in the form of*.tf files) and state files that represent the current resources. If you are using Terraform locally, without a remote state store, these files should be checked into source control for future updates.
Create a new folder and add a file called main.tf with the following content, replacing the referenced variables.
<YOUR_GCP_PROJECT_ID>: your Google Project ID.<YOUR_SNCLOUD_ORG_ID>: your StreamNative Cloud organization ID. This is typically an ID likeo-xxxxx. This can be found in your organization list or the top header of the application.
git as source control, you need to use the git init command to initialize this folder as a git project.
Step 2: Initialize the Terraform
While the above Terraform code is all needed, the module needs to be downloaded to this Terraform project. To do so, runterraform init.
This will download the module and required dependencies.
Step 3: Create a shell with the correct GCP credentials
Terraform requires GCP credentials with the proper permissions in the target project to create the resources to grant access. The permissions required by the module are all GCP project permissions, specifically to manage the GCP services, roles, and service accounts. The GCP built-in role ofEditor to the GCP project is sufficient to perform these operations.
All of the methods in Authenticating to GCP are compatible with the Terraform module.
Step 4: Run the Terraform
After initialization, and with credentials in the shell, the next step is to run the Terraform withterraform apply.
This will create a Terraform plan which shows all the resources to be created. To see an example plan, see the example plan in the GitHub readme.
Step 5: Provide the output to StreamNative
Once completed, provide the output of theterraform apply to your CSM or support representative.