Prerequisites
- Install and configure the
snctlCLI tool. - Log in to StreamNative Cloud Console.
- Create or select a cluster, tenant, and namespace where agents will run.
- Ensure your user has administrator access for the target cluster and organization.
Create a service account for agents
- In StreamNative Cloud Console, open the left navigation and choose Service Accounts.
- Click Create Service Account.
- Provide a name and optional description, then click Confirm.
Leave Super Admin unchecked so the account only receives the scoped permissions you grant later.
Authorize the service account
To make the service account work, you need to make the service account granted with proper permissions (functions, packages, produce, and consume).
To grant the service account permissions on the namespace level, follow these steps:
- Cloud Console
- Navigate to the Namespace Dashboard page by switching to the namespace workspace.
- On the Namespace Dashboard page, click Configuration on the left navigation pane.
- On the Namespace configuration page, click ADD ROLE, and select the service account that you want to authorize.
- On the drop-down menu below the service account, select the proper permissions to assign to the service account. There are six permissions in total:
-
consume: allow the service account to consume messages. -
produce: allow the service account to publish messages. -
functions: allow the service account to submit and manage functions. -
sinks: allow the service account to create and manage sink connectors. -
sources: allow the service account to create and manage source connectors. -
packages: allow the service account to upload and manage pulsar packages. If you want to submit a customized function/connector, then you will need to upload the function/connector’s JAR/NAR/Python file first, which requires thepackagespermission.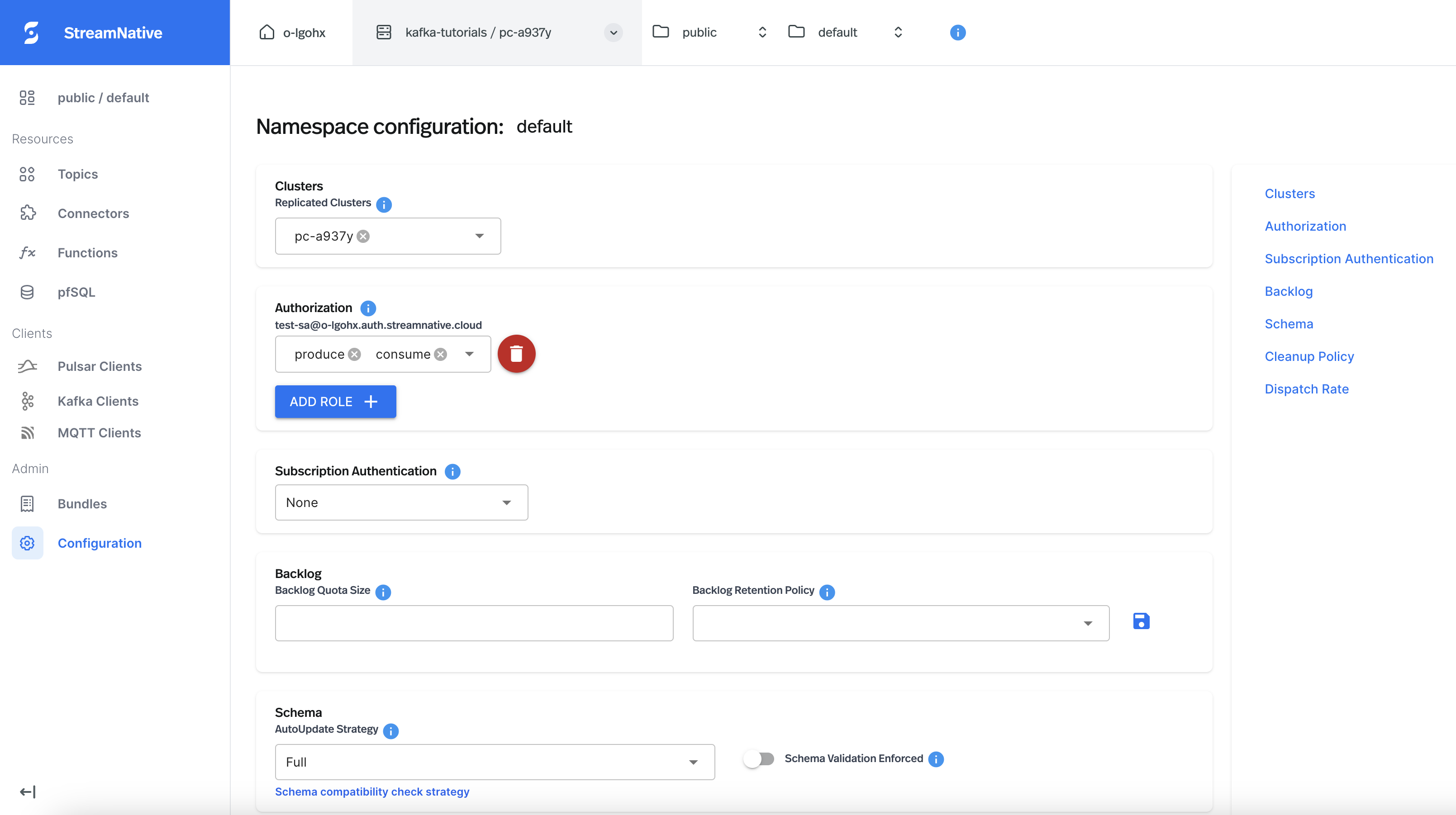
Grant access to the service account
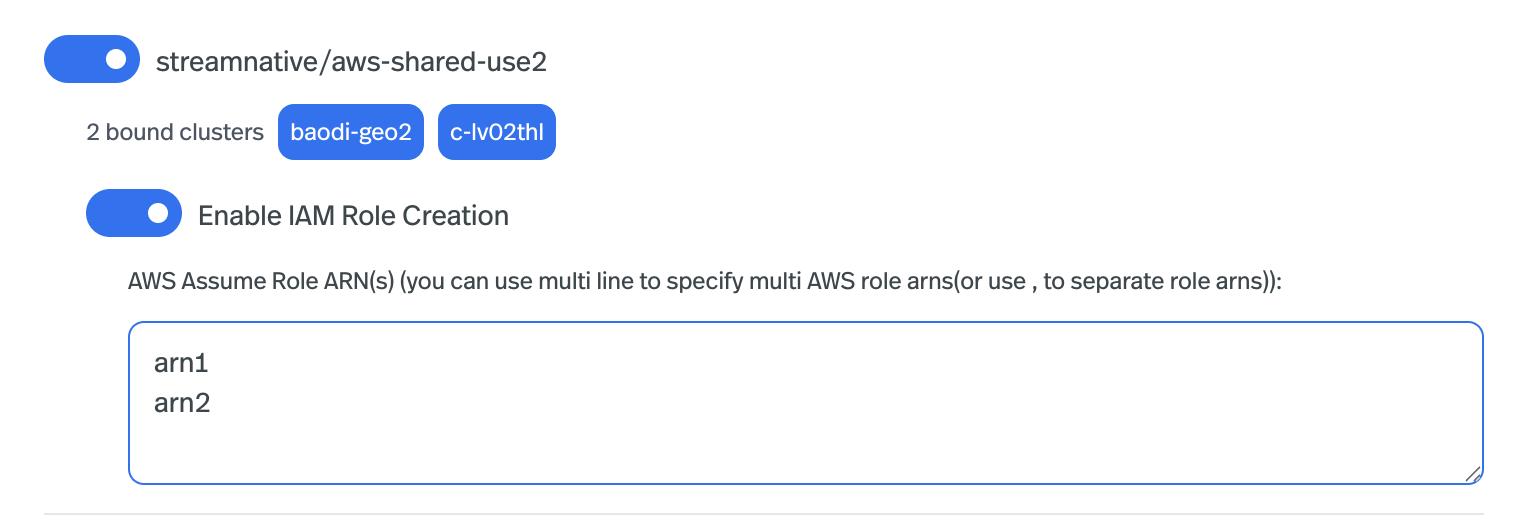
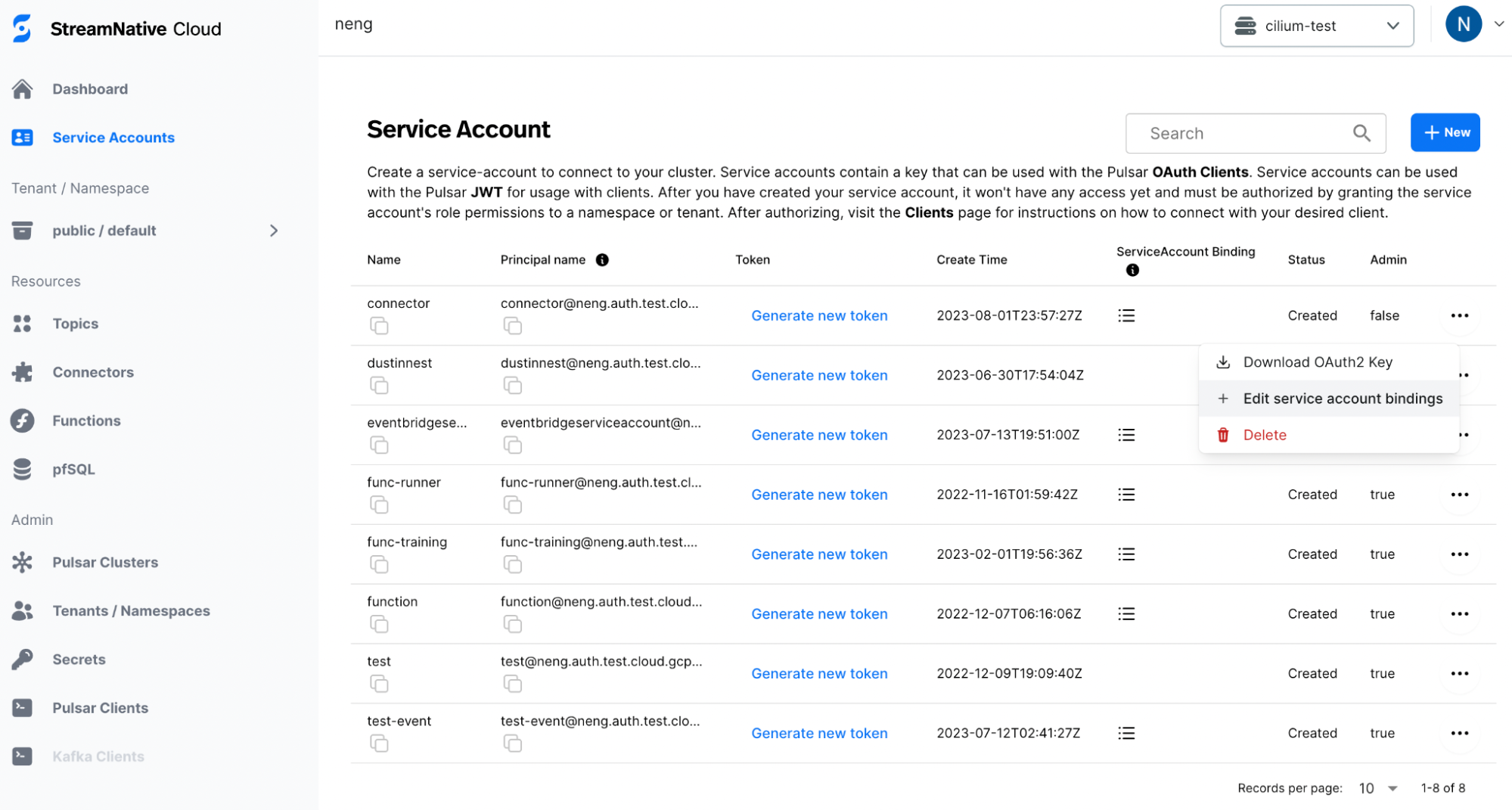
To grant the underlying infrastructure with access to the newly created service account’s OAuth2 key file, you need to create a service account binding via UI. Go to theService Accounts tab and choose the service account you want to use for running the connector. Clicking on the right button and there will be a Edit service account bindings option.
Edit service account bindings, choose the desired pool member and confirm.
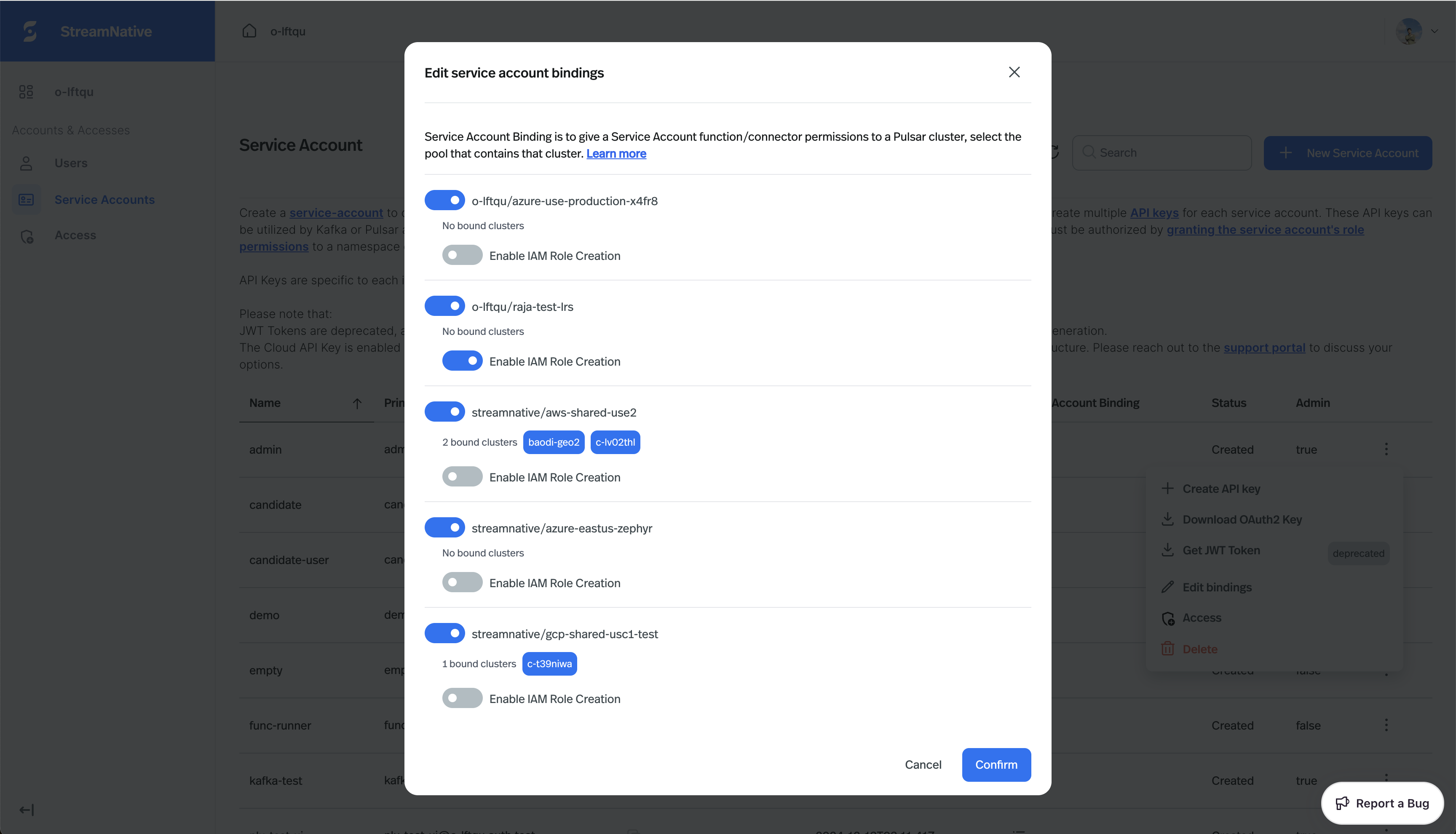
Enable IAM Role Creation option to create a separate IAM role for the service account.
Now your connector is ready to use the service account in StreamNative environments.
(Optional) Create a separate IAM role for the service account
StreamNative’s I/O components (Pulsar Functions, Pulsar Connectors, and Kafka Connectors) run as cloud-native workloads on AWS, GCP, and Azure infrastructures. Use the cloud providers’ native IAM (Identity and Access Management) services to control access to infrastructure resources such as S3, GCS, and Azure Blob Storage. This removes the need for password-based authentication for the service accounts that run connectors in StreamNative Cloud. By default, StreamNative uses a single service account perPulsarCluster for all I/O components (Pulsar Functions, Pulsar Connectors, and Kafka Connectors) to access underlying infrastructure resources. This means all I/O Components in the same cluster share one service account and the same permissions.
To enhance security and improve isolation, you can create a separate IAM role for each service account used to run connectors. This let you grant only the permissions each service account needs.
Create a separate IAM role for your service account:
- Snctl
- Console
This feature is available in snctl v1.3.0 or later.
-
Get the
PoolMembername and namespace from thePulsarClusterIn the output, find thepoolMemberRefblock, which looks like:Multiple clusters may be located in the samePoolMember. You do not need to create separate IAM roles for each cluster within the samePoolMember. -
Create a new
ServiceAccountBindingthat binds the service account to thePoolMemberAWS only: You can specify one or moreAWS Assume Role ARNsthat can be assumed by the IAM role created for the service account (repeat the flag for each ARN):The IAM role created by StreamNative will include permissions to callsts:AssumeRoleonarn1andarn2. You must still add a trust policy onarn1andarn2to allow the newly created role to assume them, an example likes below: -
(Optional) Update an existing
ServiceAccountBindingto create the IAM role -
Verify the IAM role was created successfully
Expected output (example):In the output, the
status.conditionsarray should include a condition withtype: IAMAccountReadyandstatus: "True", indicating the IAM role was created successfully.
-
Use the service account when creating I/O components
You can now select this service account in Console (or use its API key with the CLI) when creating I/O components (Pulsar Functions, Pulsar Connectors, and Kafka Connectors). The components will inherit the permissions granted to the IAM role created in the previous step.
In Azure, a Managed Identity
sab-[binding-name]-[org-id] is created;In AWS, an IAM role role/StreamNative/sncloud-role/authorization.streamnative.io/iamaccounts/IamAccount-[org-id]-sab-[binding-name] is created;In GCP, a service account with display name: IamAccount/[org-id]/sab-[binding-name] is created.Set up client tools
Use snctl to manage agents
StreamNative CLI (snctl) provides agent-aware commands that are surfaced under snctl agents.
- Set your organization:
snctl config set --organization <org-name>. - Select a cluster context:
snctl context useand choose the target cluster. - Work with agents by using the following commands (pass
--tenantand--namespaceas needed):snctl agents list– list agents in the current namespace.snctl agents create– deploy a new agent from a declarative spec and package.snctl agents update– roll out spec or code changes.snctl agents status– view runtime status.snctl agents start|stop|restart– control the running agent.snctl agents delete– remove an agent.snctl agents get– show the stored agent spec.snctl agents trigger– deliver an ad-hoc test event when supported by the agent implementation.
Use StreamNative Cloud Console
The StreamNative Cloud Console offers a guided experience for connecting client applications and reviewing agent activity. Navigate to Agents from the left panel to review existing deployments, logs, and status.What’s next?
- Review the Orca Agents overview to understand runtime architecture and capabilities.
- Package your first agent and deploy it with
snctlor the Cloud Console.