pulsar-admin or pulsar-perf CLI tool. For details, see pulsar-admin and pulsar-perf.
Authorize tenants
When you create a tenant, you can specify an administrator for the tenant.- On the left navigation pane, in the Admin section, click Tenants.
-
Click New Tenant and a dialog box displays.
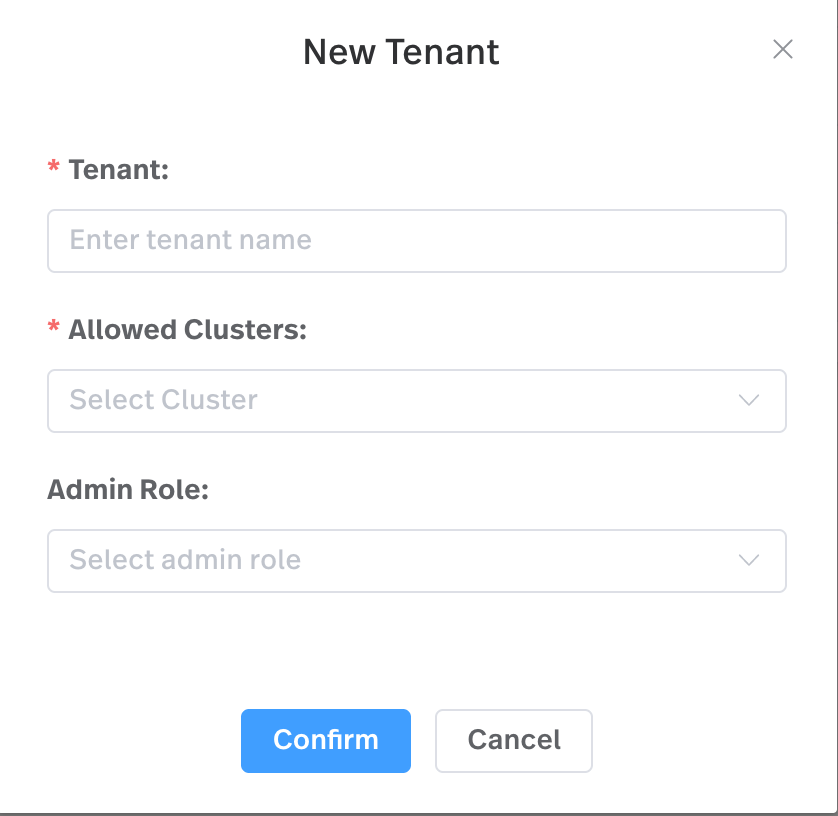
- In the Add Roles field, select a user or one or more service accounts as the administrator of the tenant.
- Click Confirm.
- On the left navigation pane, in the Admin section, click Tenants.
- Click Edit in the Action column.
- In the Add Role field, select one or more administrators for the tenant.
Authorize namespaces
To authorize a namespace through the StreamNative Cloud Console, follow these steps.- On the left navigation pane, in the Admin section, click Namespaces.
- Select the Policies tab.
-
In the Authorization area, select a role for the namespace and then grant or revoke permissions to the role in this namespace.
- consume: grant/revoke the consuming action.
- produce: grant/revoke the producing action.
- functions: grant/revoke the Pulsar functions action.
Authorize topics
To authorize a topic through the StreamNative Cloud Console, follow these steps.- On the left navigation pane, in the Resources section, click Topics.
- Click the topic name link.
- If the topic is partitioned, in the Partitions area, click the partitioned topic link.
-
Select the Policies tab and configure the authorization policies for the topic.
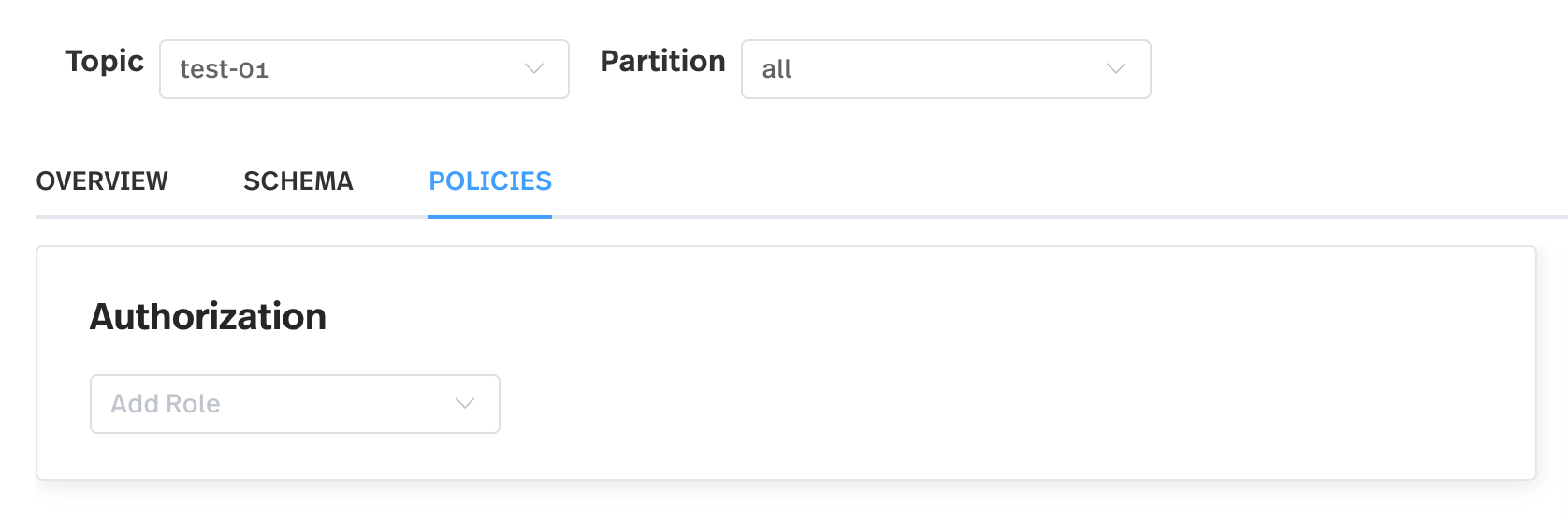
-
In the Authorization area, select a role for the topic and then grant or revoke permissions to the role in this topic by adding or deleting the following:
- consume: grant/revoke the consuming action.
- produce: grant/revoke the producing action.
- functions: grant/revoke the Pulsar functions action.