Create Secrets
The per-secret size is up to 1 Mebibyte (MiB).
- StreamNative Cloud Console
- REST API
To create a Secret using the StreamNative Cloud Console, follow these steps.
- On the left navigation pane, in the Admin area, click Secrets.
-
Click Create Secret.
-
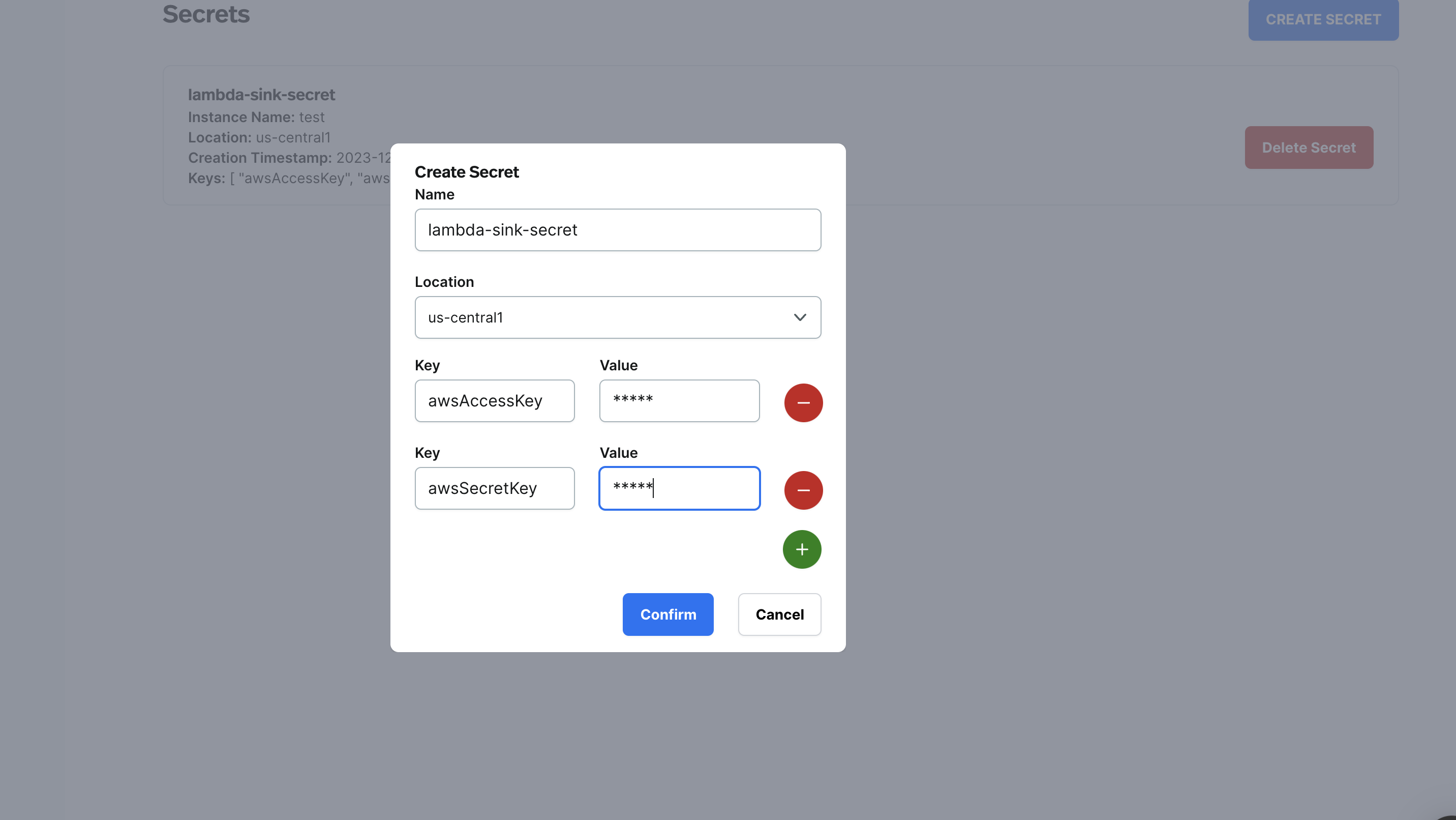
Configure the Secret.
- Name: enter the Secret name. The Secret name is unique across an organization. A secret name can contain any combination of lowercase letters (a-z), numbers (0-9), and hyphens (-).|
- Location: select a Pulsar cluster location for the Secret.
- Key: enter the key for the Secret. Each key must consist of alphanumeric characters, ’-’, ’_’ or ’.’. The serialized form of the Secret data is a base64 encoded string, representing the arbitrary (possibly non-string) data value here.
- Value: enter the value for the Secret. Each value must consist of alphanumeric characters, ’-’, ’_’ or ’.’.
- Click Confirm.
Use Secrets
After creating a Secret, you can use it when submitting a function or connector.- Enable your function/connector to access the Secret.
- Java
- Python
-
Submit the function/connector referring to the Secret.
The following is an example of using the
pulsar-adminCLI tool.
- The
SECRET1in the--secretsparameter is the name you used in your function or connector code to access the Secret value. - The
pathin the--secretsparameter is the Secret name you created. - The
keyin the--secretsparameter is the key you used in the Secret.
Delete Secrets
To delete a Secret, follow these steps.- On the left navigation pane, in the Admin area, click Secrets.
- Click Delete Secret. A dialog box displays, asking Are you sure you want to delete?
- Enter the Secret name and then click Delete Secret.