Deploy Pulsar Operators
Pulsar Operators include the BookKeeper Operator, Pulsar Operator, and ZooKeeper Operator, which can bring up a Pulsar cluster easily on Openshift.- BookKeeper Operator: provides a full management lifecycle for BookKeeper clusters.
- Pulsar Operator: manages the deployment of the Pulsar Broker and Pulsar Proxy to run Pulsar clusters.
- ZooKeeper Operator: provides a full management lifecycle for ZooKeeper clusters.
OpenShift Web Console
This section describes how to deploy Pulsar Operators using the OpenShift Web Console.Currently, you can only deploy Pulsar Operators with cluster-scoped permissions.
Prerequisites
- Install kubectl v1.16 or higher.
- Install the cert-manager.
- Deploy an OpenShift cluster.
Steps
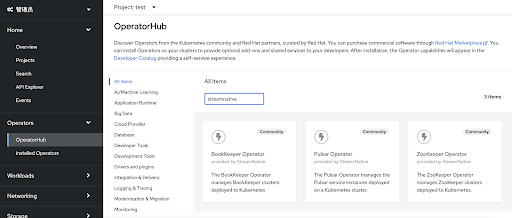
- Navigate to your OpenShift Web Console and click OperatorHub.
-
Enter “StreamNative” or “Pulsar” in the search box. There are three tiles: BookKeeper Operator, Pulsar Operator, and ZooKeeper Operator.
-
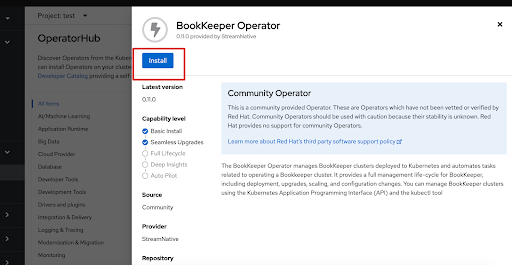
Click the BookKeeper Operator tile, and then click Install.
This step shows the BookKeeper Operator as an example.
-
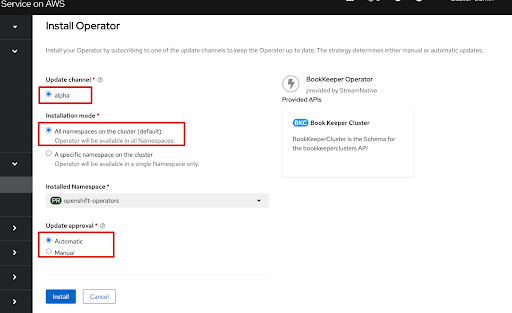
Customize the configurations.
- Installation mode
- All namespaces on the cluster(default): deploy the Pulsar Operators with cluster-scoped permissions.
- A specific namespace on the cluster: deploy the Pulsar Operators with namespace-scoped permissions. Currently, this option is not supported because it needs to pass the parameter through an environment variable.
- Updated Approval
- Automatic: automatically install or update the Pulsar Operators.
- Manual: manually install or update the Pulsar Operators.
- Installation mode
-
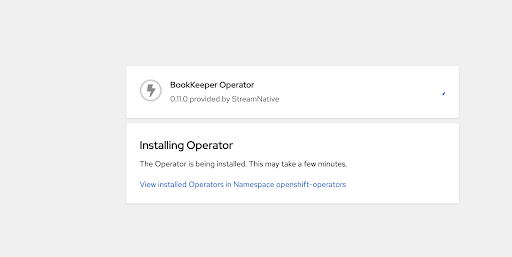
Click Install. A page displays, showing the BookKeeper Operator installation process.
-
After the BookKeeper Operator is installed, you can see the new status Installed operator - ready for use.
- Repeat Steps 3 through 6 to install the Pulsar Operator, and then repeat the steps for the ZooKeeper Operator.
-
Confirm that all Pulsar Operators are running. You can find the Pods in the openshift-operators namespace.
CLI
This section describes how to deploy Pulsar Operators using the Command Line Interface (CLI) tool.You can deploy Pulsar Operators with either cluster-scoped permissions or namespace-scoped permissions.
Prerequisites
- Install kubectl v1.16 or higher.
- Install Helm v3.0 or higher.
- Install the cert-manager.
- Deploy an OpenShift cluster.
- Prepare the Pulsar Operators v0.10.3 or higher.
Steps
To deploy Pulsar Operators using the CLI tool, you can define the following options in yourvalues.yaml YAML file.
- [1]
watchNamespace: describe the namespace where the Controllers watch updates to Pulsar components. - [2]
<component>: represent the component to configure, such as the Pulsar broker, Pulsar Proxy, and so on. - [3]
serviceAccount: provide an identity for processes that run in a Pod. - [4]
clusterRole: describe whether to grant cluster-scoped permissions to the service account. By default, it is set totrue.
- Pulsar Operators with cluster-scoped-permissions
- Pulsar Operators with namespace-scoped-permissions
To deploy Pulsar Operators with cluster-scoped permissions, you can set an empty string to the
watchNamespace option and set the clusterRole option to true.This example shows how to deploy Pulsar Operators with cluster-scoped permissions.-
Create a Kubernetes namespace.
- Install the Pulsar Operators.
The
pulsar-operator chart provides default values for options that are used to install the Pulsar Operators with cluster-scoped permissions. You can customize the file according to your configuration.-
Confirm that all Pulsar Operators are running.
Deploy StreamNative Platform Chart
Before deploying StreamNative Platform on OpenShift, you need to install the Vault Operator, configure the Security Context Constraints (SCCs), and disable Pulsar monitoring components (including Prometheus, Grafana, and so on).Enable OpenShift Security Context Constraints
SCCs allow you to control permissions for the Pulsar Pods. You can either use the default SCC or use an existing SCC.- Use the default SCC
- Use an existing SCC
If you do not have a SCC yet, a SCC is automatically created when you deploy StreamNative Platform using the Helm Chart. You can set the
openshift.scc.create option to true in your values.yaml YAML file and then update the resources.- [1]
scc.enabled: enable SCC for StreamNative Platform. - [2]
scc.create: create a SCC automatically.
Disable monitoring components
OpenShift is shipped with monitoring components. Therefore, you must disable Pulsar monitoring components by using themonitoring.<component> option.
Examples
This example shows how to deploy StreamNative Platform on OpenShift with the default SCC and namespace-scoped permissions.-
Create a Kubernetes namespace for your Pulsar cluster.
This example shows how to create a Kubernetes namespace
app-snfor your Pulsar cluster. -
Define a YAML file.
This is a sample YAML file. You should customize the file according to your configuration.
-
Apply the YAML file to deploy StreamNative Platform.