OAuth/OIDC Federation is currently in Private Preview and is only available for BYOC Pro clusters. If you are interested in this feature, please join our Early Access Program.
Key Features
- Manage application identities and credentials through your own identity provider
- Authenticate to StreamNative Cloud resources using secure, short-lived JSON Web Tokens (JWTs)
- Leverage StreamNative’s OIDC Federation service to securely integrate with your identity provider using standards-compliant tokens based on the OAuth 2.0 Authorization Framework [RFC 6749] and OpenID Connect (OIDC)
- Configure identity pools to map group memberships and other attributes to access policies (RBAC or ACLs)
Feature availability and limitations
- This feature is currently available only for BYOC Pro clusters for Private Preview. To get access, please join our Early Access Program.
- Identity pools and the ACLs for identity pools can be managed only by using
snctlor the Cloud API.
OIDC Federation Flow
The following diagram illustrates the OIDC Federation flow for an organization.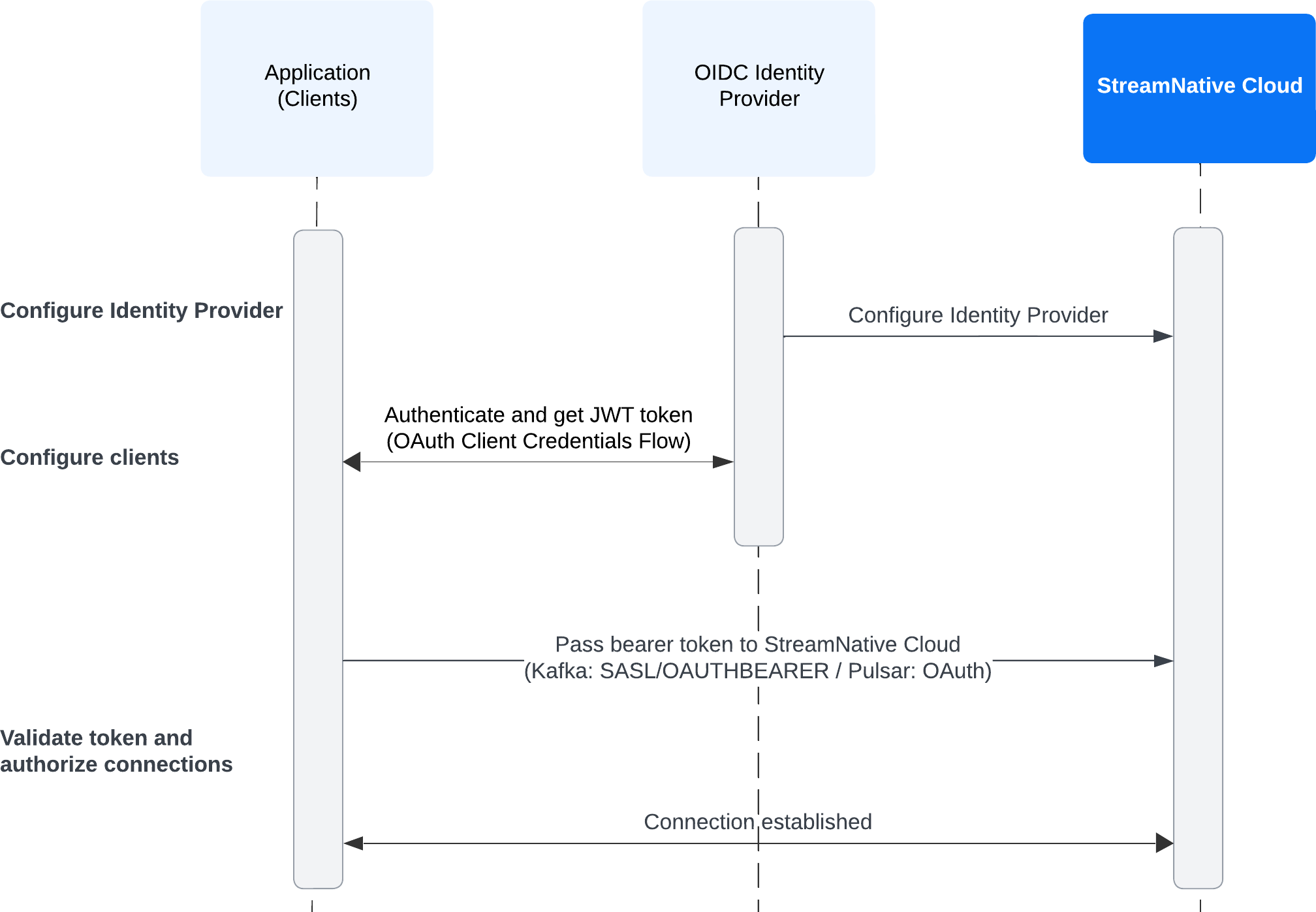
-
Configure OAuth/OIDC Identity Provider:
To use OIDC Federation, you must first establish trust between StreamNative Cloud and your identity provider by adding it as a trusted identity provider in StreamNative Cloud. This involves:
- Defining the identity provider type
- Creating a trust relationship between StreamNative Cloud and your identity provider
- Adding the claims needed for authentication and authorization
- Create an Identity Pool and Access Policies: Create an identity pool to represent a group of external identities. This allows you to assign appropriate access levels through policies.
- Configure Clients to Use Your Identity Provider: Obtain the Client ID and Client Secret from your identity provider to configure clients for OAuth2 authentication. For more details, see Use OAuth to Authenticate to StreamNative Cloud.
-
Token Validation and Authorization:
StreamNative Cloud validates incoming tokens using the trust JSON Web Key Set (JWKS), extracts the authenticated ID (
sub) or other configured claims, and matches the authenticated identity to the appropriate identity pool for authorization.